
No Phishiing Allowed
That’s not a misspelling. It’s one of those technical terms you need to know. Phishing is a fraudulent attempt, usually made through email, to steal your personal information. The best way to protect yourself from phishing is to learn how to recognize a phish.
Phishing emails usually appear to come from a well-known organization and ask for your personal information – such as credit card number, social security number, account number or password. Often, phishing attempts appear to come from sites, services and companies with which you do not even have an account.
In order for Internet criminals to successfully “phish” your personal information, they must get you to go from an email to a website. Phishing emails will almost always tell you to click a link that takes you to a site where your personal information is requested. Legitimate organizations (for example, Babson College) would never request this information of you via email.
At first glance, these messages appear to be from a legitimate source, but a closer inspection usually reveals numerous flaws. Here’s what to look for in a phishing email:
- Generic greeting. Phishing emails are usually sent in large batches. To save time, Internet criminals use generic names like “Dear Wells Fargo Online Customer.” If you don’t see your name, be suspicious!
- Request for personal information. The point of sending phishing email is to trick you into providing your personal information. If you receive an email requesting your personal information, it is probably a phishing attempt.
- Sense of urgency. Internet criminals want you to provide your personal information now. They do this by making you think something has happened that requires you to act fast.
- Forged link. Even if a link has a name you recognize somewhere in it, it doesn’t mean it links to the real organization. Roll your mouse over the link and see if it matches what appears in the email. If there is a discrepancy, don’t click on the link. For example:
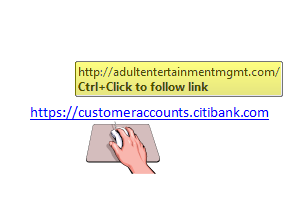
If it’s a phishing email, delete it!
Information taken from: http://www.phishtank.com